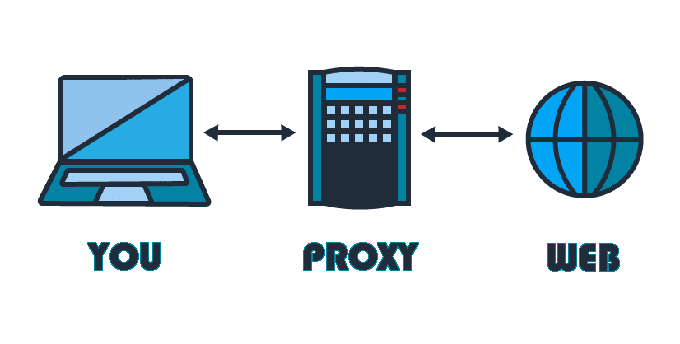
A proxy server is a computer that acts as an intermediary between an endpoint device and the Internet. A proxy server is a type of firewall that sits on the network, intercepting all requests to access the Internet.
A Wow Proxy Server is a free proxy service which allows users to bypass firewall restrictions and get access to any website they want.
In this article, we will be discussing what a Wow Proxy Server is, how it works and its benefits.
What are the Different Types of Proxy Servers?
There are many types of proxy servers. The type of proxy server that is used in a given situation depends on the requirements and the needs of the user.
The most common type of proxy server is the SOCKS proxy server. SOCKS proxies are usually used for web browsing and other internet related tasks. They allow users to bypass firewalls and access websites that are blocked in their region. Another common type of proxy server is the HTTP Proxy Server, which can be used to cache data, filter content, or provide anonymity online. There are also SSL proxies which encrypts all traffic between a user’s computer and the remote server it communicates with to ensure privacy and security. There are also reverse proxies which can be used as load balancers or content caches to speed up a website’s performance by reducing traffic congestion on its servers, while others use them as caching servers for web applications like CDNs (Content Delivery Networks).
There are many different types of proxy servers. The most common type is the web proxy. Web proxies are used to change your IP address and access restricted content on the internet.
The SOCKS5 proxy server is also a popular type of proxy server, like those proxy-sale.com/en/ provides. It’s mainly used for changing your IP address and accessing restricted content on the internet.
How Does a Proxy Server Work?
A proxy server is a computer system or device that acts as an intermediary between the user and the destination server. The user connects to the proxy server, then requests a connection to a different server. The proxy manages all of this, so the user does not need to be aware of any of it.
The term “proxy” is used because it acts as an intermediary for requests from one party and provides those requests to another party, who will fulfill them.
What Happens When You Use a Proxy?
A proxy is a common tool used to access blocked websites, such as social media sites, which are blocked in certain countries. Proxies work by routing your connection through another server and making it appear like the server you are connecting to is the one you want to visit.
There are many benefits of using a proxy including: bypassing censorship, accessing blocked websites, protecting your privacy and being able to browse anonymously. However, there are also disadvantages such as slower browsing speeds and less stable connections.
Why Do I Need to Use a VPN or Proxy Server?
In this day and age, it is important to use a VPN or proxy server in order to protect your data and privacy. You can find out about the reasons for needing a VPN or proxy server below.
A VPN or proxy server is needed in order to protect your data and privacy. The internet is full of hackers and people who want to steal information from you. They can do this by hacking into your device such as a laptop, tablet, smart phone, etc. A VPN or proxy server will keep these hackers away from your information.
Conclusion & Tips for Choosing the Right Tunneling Software for You
Choosing the right tunneling software for your company can be a challenge. There are many factors to consider before you make a decision.
The first thing to do is to identify the needs of your company and then find the tunneling software that best meets them. For example, if you need to access remote networks, you should look for network tunneling software rather than file transfer software.
Next, consider how much control you want over the process of selecting and setting up your tunneling software. If you want full control, choose a self-configuring and self-installing option that doesn’t require any additional IT involvement.

